Top 10 cybersecurity vulnerabilities and exploits threatening corporate systems
by Bija Knowles
What are the most common digital threats challenging companies today? Ignoring new software security patches, unsupported systems and a lack of strong permission and user access controls are all part of the problem. This is according to Protiviti's 2018 Security Threat Report, which looks at the most common digital threats in today's cyber security landscape. It also found that financial service firms have the highest vulnerability rate to cyberattacks. The report also lists the top 10 external exploits (see Protivit's graphs below).
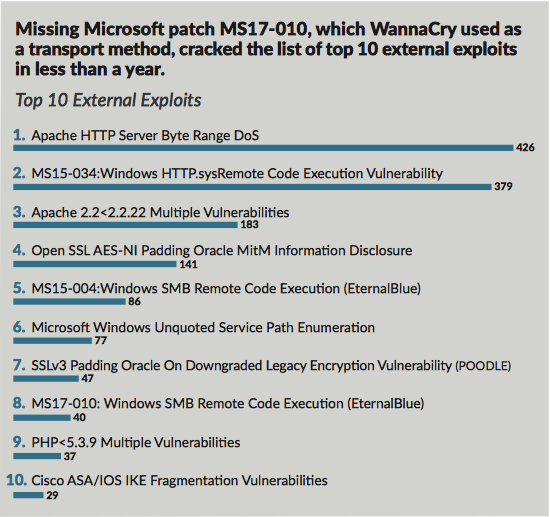
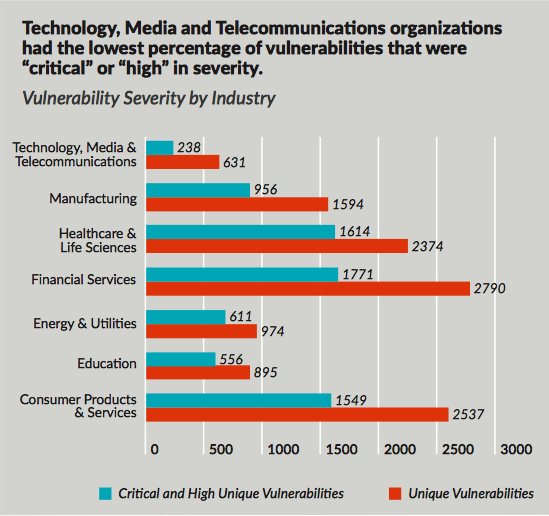
Problems that can be rectified
The key takeaways from the report include:
- vulnerabilities that can be easily patched are not being fixed in a timely manner, particularly within applications;
- organisations are still running a significant number of unsupported systems, greatly increasing the risk for breaches;
- there have been consistent challenges with SSL, especially with weak ciphers and diversions;
- every few years, a major critical exploit comes along that has a dramatic impact on the security landscape (e.g. Heartbleed, Shellshock);
- just under half of the vulnerabilities identified during testing have publicly available exploit code (as of the time of testing); and
- companies in the consumer products; financial services; healthcare and life sciences; technology, media and telecommunications; manufacturing; and energy industries are the most vulnerable.
The firm analysed vulnerability scans and tests of IT systems and infrastructure at over 500 organisations. Protiviti's Scott Laliberte said: “Most of the issues we identified in our assessment can be easily rectified by taking a proactive and programmatic approach to cybersecurity. By evaluating security posture on a periodic basis and implementing changes to update IT procedures, companies can significantly lower the risks associated with potential security breaches and attacks. Unfortunately, as the threat landscape has become more perilous, it’s only a matter of ‘when’ your organisation will get targeted, so we can’t overstate the importance of implementing continuous improvement within your security program immediately.”
5 security principles
The report also identified five basic security principles to reduce the risk of a breach:
- Maintain strong permission and user access controls: By periodically checking networks and default permissions/credentials, organizations can reduce the likelihood of a hacker gaining easy access to a network.
- Provide employee security awareness: Inform employees of the latest security threats and social engineering techniques, how they can protect themselves, and what the organization is doing to mitigate these risks.
- Implement a patch management program: Organizations should use automated tools to both identify and apply patches within network devices, operating systems and applications. For systems that cannot be upgraded or patched, compensating controls (e.g., VLAN’s or firewalls) should be implemented to protect the rest of the network.
- Ensure strong system configuration management: Be sure to look into areas such as password and audit policies, services, and file permissions, as these should be controlled through the configuration management process.
- Conduct periodic penetration testing: Penetration testing and ongoing vulnerability management across various pieces of IT infrastructure can help organizations identify security vulnerabilities and stay up-to-date with the latest tricks and techniques attackers are using.
Like this item? Get our Weekly Update newsletter. Subscribe today
