How to detect and prevent fraud ….. Sometimes
by Jack Large
Fraud is part of business. It is a booming industry and so is fraud prevention - reports are published almost daily. The latest reports include:
- Ravelin’s Guide to Fraud detection for the on-demand economy which contained these useful ideas:
- What corporates should expect from their Payment Service Providers:
- An understanding of the basic fraud checks that a PSP undertakes
- An understanding of how the PSP handles 3DS and any other Strong Customer Authentication protocols
- Critically how a PSP can provide data back to the merchant to help with their own fraud detection
- How a PSP logs historical data, especially how it provides information on failed transactions
- How a PSP provides chargeback data (via .csv or through an API) and how it associates a chargeback with the original transaction.
- Automate fraud detection using machine learning but need to set correct fraud threshold, and vary the threshold for each market.
- What corporates should expect from their Payment Service Providers:
- TIS white paper: the four elements in the TIS security methodology:
- Information security
- Business continuity
- Infrastructure
- TIS applications.
- Kount’s 6th Annual Mobile Payments & Fraud report:
- Findings:
- Channel with greatest risk:
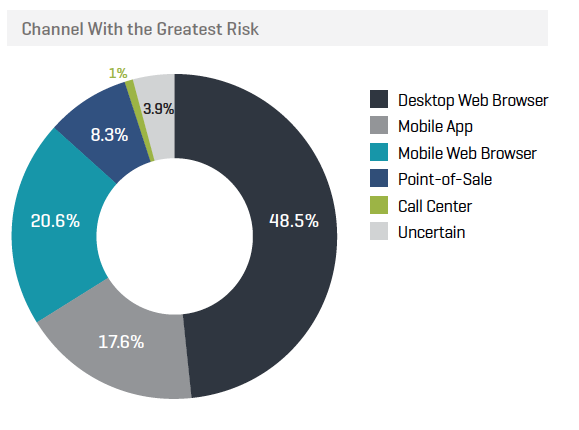
- Mobile fraud is increasing
- Tools to tackle mobile fraud include:
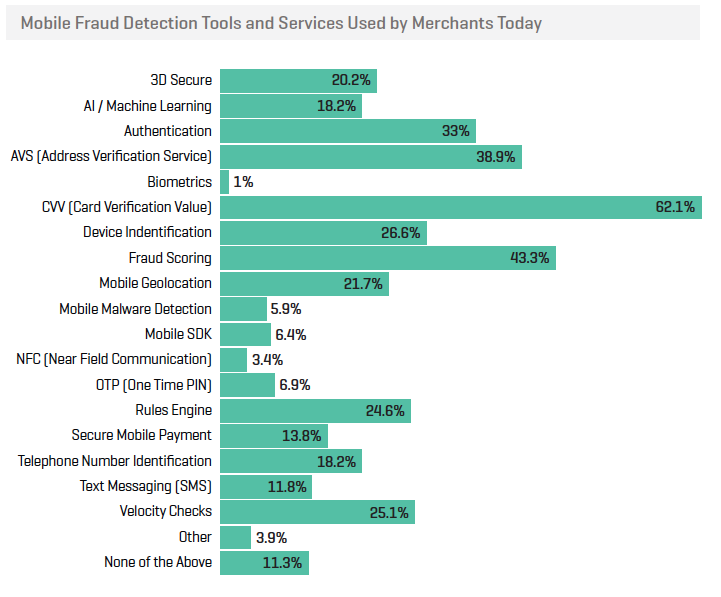
- Source & Copyright©2018 - Kount
- Channel with greatest risk:
- Findings:
Cyberfraud prevention checklists
CTMfile’s recommends using these Checklists to keep cyber fraudsters at bay:
- International Chamber of Commerce 'Cyber security guide for business', presenting a number of principles, strategies and actions that can help companies put a cyber security framework into practice
- The board Checklist: the vital questions
- ’10 steps to Cyber security from UK’s GCHQ’ (UK Government Communications Headquarters) who monitor the Internet and many other networks
- SANS (System Administration, Networking, and Security Institute) ‘Critical Security Controls’ —a short list of controls developed by security experts world-wide based on practices that are known to be effective in reducing cyber risks
- NIST (National Institute of Standards and Technology) Framework for Improving Critical Infrastructure Cybersecurity—combines a variety of cybersecurity standards and best practices together, see
- Shared Assessments—an organization that develops assessment questionnaires for use by its members, see
- ACFE’s Fraud Prevention Checklist, see
- ’40 questions you should have in your vendor security assessment’ from BITsight which shows how to monitor and manage vendor security.
CTMfile take: Fraud seems to be endemic, but it doesn’t have to be. Use these Checklists.
Like this item? Get our Weekly Update newsletter. Subscribe today
